Your accounting software is both your greatest asset and your biggest vulnerability. Cybercriminals are constantly advancing their tactics to breach your accounting software security, putting your business's reputation and bottom line at risk.
A single breach can cost thousands, disrupt operations, and shatter customer trust and your reputation.
But I say that to inform — not to scare. With the right security measures, you can shield your accounting data from threats. In this article, I'll walk you through 15 practical, effective tips to bulletproof your financial data and outsmart the cyber bad guys.
- Implement Strong Password Policies
- Use Multi-Factor Authentication (MFA)
- Encrypt Data at Rest and in Transit
- Regular Software Updates and Patch Management
- Employee Access Control and Permissions
- Regular Data Backups
- Network Segmentation
- Implement Intrusion Detection Systems (IDS)
- Conduct Regular Security Audits
- Use Virtual Private Networks (VPNs) for Remote Access
- Implement Email Security Measures
- Implement Endpoint Protection
- Implement Secure API Integrations
- Educate Employees on Cybersecurity Best Practices
- Adopt Zero Trust Architecture
1. Implement Strong Password Policies
"Password123" just doesn't cut it anymore. Weak passwords are like leaving your front door wide open. Cybercriminals can quickly exploit these to access and damage your financial data.
So, how do we fix this? By implementing a rock-solid password policy. Here's what you need to do:
- Require passwords to be at least 12 characters long
- Mix it up with uppercase, lowercase, numbers, and symbols
- Ban common words and easily guessable info (like names and birthdates)
- Enforce password changes every 90 days
- Use a password manager to generate and store complex passwords
How Dropbox Cracks Down on Weak Passwords
Dropbox takes password security seriously. They:
- Require a minimum of 8 characters, but strongly encourage longer ones.
- Use zxcvbn, an open-source password strength estimator, to help users create robust passwords.
- Offer two-factor authentication for an extra layer of security.
If Dropbox, with its millions of users, prioritizes password strength, shouldn't you?
2. Use Multi-Factor Authentication (MFA)
Having strong passwords is a solid start… But not foolproof. Enter Multi-Factor Authentication (MFA), your password’s personal bouncer. Even if a hacker cracks your password, they can’t access your account without this second verification step.
How MFA works:
- Enter your username and password.
- Pass a secondary verification step:
- A code via SMS or an authenticator app.
- Biometric data like a fingerprint or facial recognition.
- A physical security key.
Though setting up MFA might seem like a hassle, it boosts your account security by 99.9%. Many accounting software platforms offer MFA for free, so skipping it is like leaving your data — and money — vulnerable.
3. Encrypt Data at Rest and in Transit
Think of encryption as your data's invisible cloak, turning your financial info into a scrambled secret message only authorized eyes can read. For data security, it's crucial to encrypt data both when it's sitting idle (at rest) and as it zips across the internet (in transit).
Threat: Unencrypted data is an easy target for cyber thieves. Whether intercepted during transmission or accessed in storage, it can be readily used or sold.
Impact:
- Exposure of sensitive financial information.
- Increased risk of identity theft and fraud.
- Legal consequences for failing to protect client or customer data.
Data at rest: This is your info chillin' on your computer or in the cloud. Encrypt it with:
- Full-disk encryption on all devices
- Encrypted cloud storage services
- Built-in encryption features in your accounting software
Data in transit: This is your data when it's on the move. Protect it by:
- Using HTTPS for all web-based accounting software
- Employing secure file transfer protocols (SFTP or FTPS) when moving data
- Setting up a VPN for remote access
Check if your accounting software offers end-to-end encryption. This means your data is encrypted from the moment it leaves your device until it reaches its destination. It's the gold standard of data protection.
QuickBooks Online's Encryption Game
Intuit, the company behind QuickBooks Online, doesn't mess around when it comes to encryption.
- They use 128-bit SSL encryption for all data in transit.
- For data at rest, they employ multiple layers of protection, including AES 256-bit encryption for stored data.
- They even encrypt data between their own data centers.
It's like Fort Knox, but for your financials.
4. Regular Software Updates and Patch Management
Let's talk about those pesky software updates you keep putting off. You know, the ones that always seem to pop up when you're in the middle of something important?
Those updates aren't just about shiny new features. They're often patching up security holes that hackers are itching to exploit.
So, how do you stay on top of this?
- If possible, set your accounting software to update automatically
- If not, check for updates weekly and apply them ASAP
- Don't forget about your operating system and other related software
- Keep an eye out for security bulletins from your software provider
But beware: updates can sometimes break things. That's why you need a patch management strategy:
- Test updates in a non-production environment first
- Back up your data before applying updates
- Schedule updates during off-hours to minimize disruption
- Have a rollback plan in case something goes wrong
Microsoft and WannaCry’s Ransomware Attack
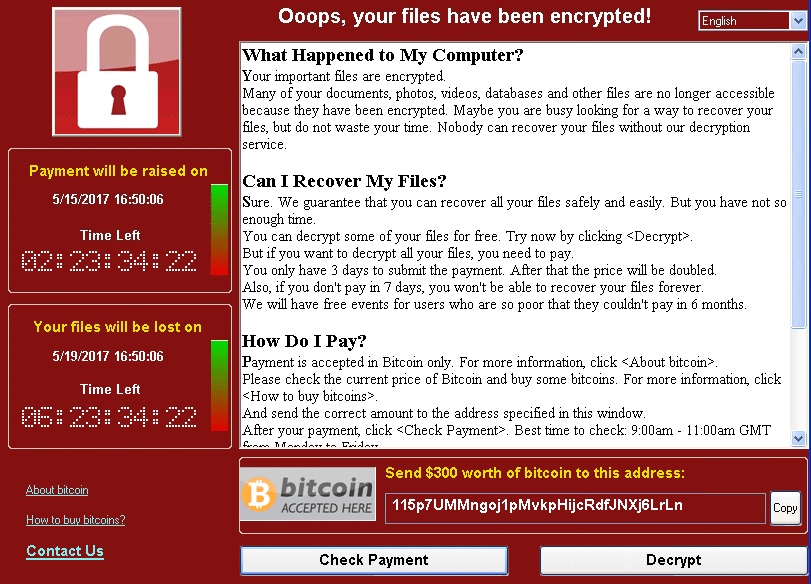
In 2017, the WannaCry (aka WannaCrypt… aka WannaDecryptor) ransomware attack exploited vulnerabilities in outdated Windows systems. After infecting a Windows computer, it encrypted files on the hard drive, rendering them inaccessible to users. It then demanded a ransom payment in Bitcoin for decryption.
Microsoft had already released a Server Message Block (SMB) patch for the vulnerability about two months before this attack, and those who had updated their systems were protected from the attack. This example underscores the critical nature of staying current with software updates to safeguard data.
5. Employee Access Control and Permissions
Let's talk about who gets to see what in your accounting software. It's not about trust; it's about smart security.
Think of your financial data like a high-security building. You wouldn't give every employee a master key, right? Same goes for your accounting software.
Here's how to lock it down:
- Use the principle of least privilege: Give employees access only to what they absolutely need for their job
- Set up role-based access controls (RBAC)
- Regularly review and update these permissions
- Implement strong user authentication for each account
- Use single sign-on (SSO) if possible to manage access across multiple systems
But it's not just about setting it up once and forgetting about it. You need to stay on top of things:
- Remove access immediately when an employee leaves
- Adjust permissions when someone changes roles
- Conduct regular audits of who has access to what
Here's a real scenario: Your sales team probably needs to input customer data, but do they need to see payroll info? Nope. Your HR folks need employee data, but full access to financial reports? Probably not.
6. Regular Data Backups
Regularly tidying up your financial data is like having an insurance policy for your business's digital assets.
In a cyberattack, natural disaster, or human error, having up-to-date backups can be the difference between a quick recovery and a prolonged, costly downtime.
So, how do we avoid this nightmare scenario?
- Follow the 3-2-1 rule: 3 copies of your data, on 2 different types of media, with 1 copy off-site
- Automate your backups — don't rely on someone remembering to do it
- Encrypt your backups (yep, I’m harping on encryption again)
- Regularly test your backups to make sure they actually work
GitLab Data Loss
GitLab experienced a significant data loss incident in 2017 due to an accidental deletion during a database replication process. That caused them a downtime of over 36 hours — bad, but could’ve been worse. Fortunately, their rigorous backup policy allowed them to restore most of the lost data.
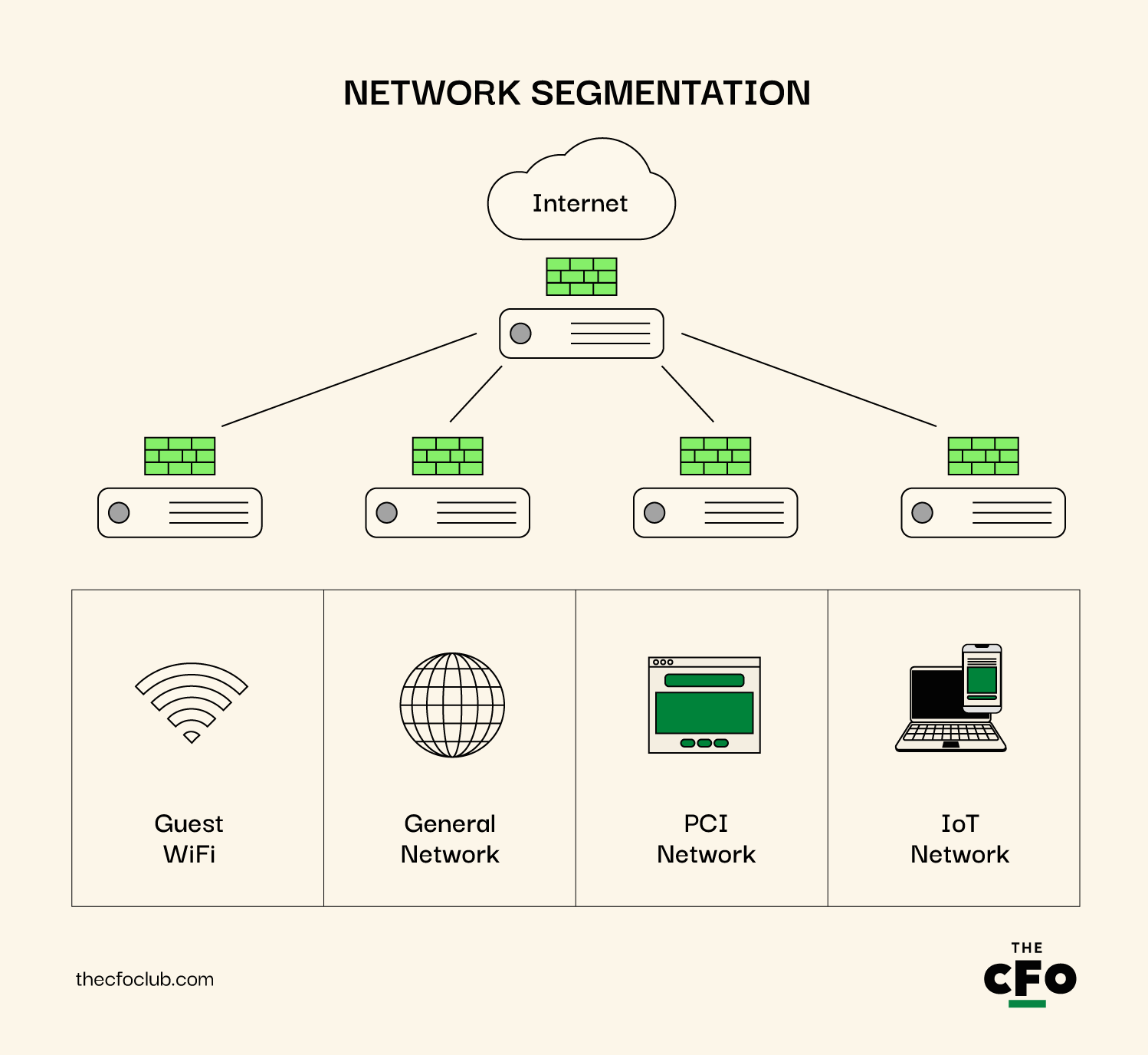
7. Network Segmentation
Let's talk about dividing and conquering… your network, that is. Network segmentation is like building secure rooms inside your data fortress.
Here's why it matters: If a hacker breaches one part of your network, you don't want them to have free rein over everything. It's like containing a fire in one room instead of letting it burn down the whole house.
So, how do you slice and dice your network?
- Separate your accounting systems from the general network
- Use virtual LANs (VLANs) to create logical divisions
- Set up firewalls between network segments
- Implement strict access controls between segments
It's not just about external threats. Network segmentation also protects you from insider risks.
Consider this setup:
- Accounting segment: Only for finance staff and systems
- General business segment: For day-to-day operations
- Guest network: For visitors or personal devices
- IoT segment: For all those smart devices that could be security weak points
How MITRE Contained a Cyberattack With Micro-Segmentation
In April 2024, MITRE got hit with a cyberattack that managed to sneak past their VPNs and multifactor authentication. But thanks to their smart setup with network segmentation, they were able to isolate the compromised areas quickly.
They used something called micro-segmentation, part of their zero trust approach, which really helped by cutting off any communication between the infected systems and the clean ones. This move was crucial in keeping the breach from spreading further.
No organization is immune from this type of cyberattack, not even one that strives to maintain the highest cybersecurity possible.
The threats and cyberattacks are becoming more sophisticated and require increased vigilance and defense approaches.
8. Implement Intrusion Detection Systems (IDS)
Intrusion Detection Systems (IDS) are like the high-tech alarm systems of your accounting software, alerting you to any suspicious activity or potential breaches. They:
- Spot potential threats in real-time
- Alert you to suspicious activity
- Help you respond quickly to actual breaches
- Keep a log of network activity for forensic analysis
However, not all IDS are created equal. You've got options:
- Network-based IDS (NIDS): Monitors traffic on your entire network
- Host-based IDS (HIDS): Watches for suspicious activity on specific devices
- Signature-based detection: Looks for known patterns of malicious activity
- Anomaly-based detection: Flags unusual behavior based on normal patterns
Be wary not to think of IDS as a security team: They’re about detection, not prevention. It's the alarm system, not the lock on the door. You need both.
9. Conduct Regular Security Audits
Think of security audits as routine health check-ups for your accounting software, identifying vulnerabilities before they escalate into serious threats. These audits ensure your security measures are current and robust.
Here's why you need to do this:
- Spot system vulnerabilities
- Ensure compliance with regulations
- Stay ahead of evolving threats
- Guide security improvements
Now, let's break down what a security audit should cover:
- Review of access controls and user permissions
- Assessment of data encryption practices
- Evaluation of network security measures
- Check on software update and patch management
- Review of backup and recovery procedures
- Assessment of physical security measures
Don't just audit your tech. Look at your processes, too. Are employees following security protocols? Is sensitive data being handled correctly?
Frequency matters. At a minimum, do a full audit annually. But for critical systems like your accounting software? More frequent checks are smart.
10. Use Virtual Private Networks (VPNs) for Remote Access
Let's talk about working from... well, anywhere. Remote work is great, but it can be a security nightmare if you're not careful. Meet VPN: your personal secure tunnel through the Wild West of public Wi-Fi.
Here's why VPNs are a must-have:
- Encrypts internet connection
- Hides IP address
- Prevents eavesdropping on public networks
- Allows secure access to your company's network from anywhere
But not all VPNs are created equal. Here's what to look for:
- Strong encryption (at least AES-256)
- No-logs policy
- Kill switch feature
- Multi-factor authentication
Now, here's where people often mess up: They only use VPNs for "important" stuff. Nope. Use it all the time when working remotely. That innocent-looking coffee shop Wi-Fi? It could be a hacker's playground.
11. Enforce Email Security Measures
Email is the lifeblood of business communication, but it's also a hacker's favorite hunting grounds. Time to turn your inbox from a potential security nightmare into a digital fortress.
Here's why email security is non-negotiable:
- Phishing attacks often start with a dodgy email
- Sensitive financial data frequently zips through email
- Malware loves to hitch a ride on email attachments
So, how do I recommend bulletproofing your emails?
- Use strong spam filters to catch obvious threats
- Implement email encryption for sensitive data
- Enable sender policy framework (SPF) to prevent email spoofing
- Set up Domain-based Message Authentication, Reporting & Conformance (DMARC)
- Use secure file-sharing instead of email for large or sensitive files
Remember, the weakest link in email security is often the human factor. Regular training on spotting phishing attempts and handling sensitive data is crucial. We use NINJIO for our regular training sessions, and — I never thought I’d say this about a cybersecurity information service — I love it.
12. Implement Endpoint Protection
End-point devices like computers, tablets, and smartphones are the gateways through which users interact with your accounting software. Ensuring these devices are secure is crucial because they are often the first targets in cyberattacks.
Here's why endpoint protection matters:
- Blocks malware before it can infect your network
- Detects and responds to suspicious activity in real-time
- Prevents data loss from compromised devices
- Gives you visibility into all devices accessing your system
To fortify your endpoints, follow this process:
- Install robust anti-malware and antivirus software on all devices
- Use endpoint detection and response (EDR) solutions for advanced protection
- Implement device control policies (e.g., restricting USB usage)
- Enable full-disk encryption on all endpoints
- Keep all endpoint software and operating systems up-to-date
13. Implement Secure API Integrations
Secure API integrations act like well-trained diplomats: they ensure that data can safely travel between your accounting software and other systems, maintaining strict protocols to protect the integrity and confidentiality of the data exchanged.
Here's why API security is crucial:
- APIs can provide direct access to sensitive financial data
- Insecure APIs can be exploited for data breaches
- Many modern accounting workflows rely heavily on integrations
- API vulnerabilities can compromise multiple connected systems
To lock down your APIs:
- Use strong authentication for all API access (OAuth 2.0 is a good start)
- Implement rate limiting to prevent abuse
- Encrypt all data transmitted via APIs
- Regularly audit and update API access tokens
- Monitor API usage for unusual patterns
People often slip up by forgetting about third-party APIs they're using. These need attention, too!
How Xero Excels at API Security
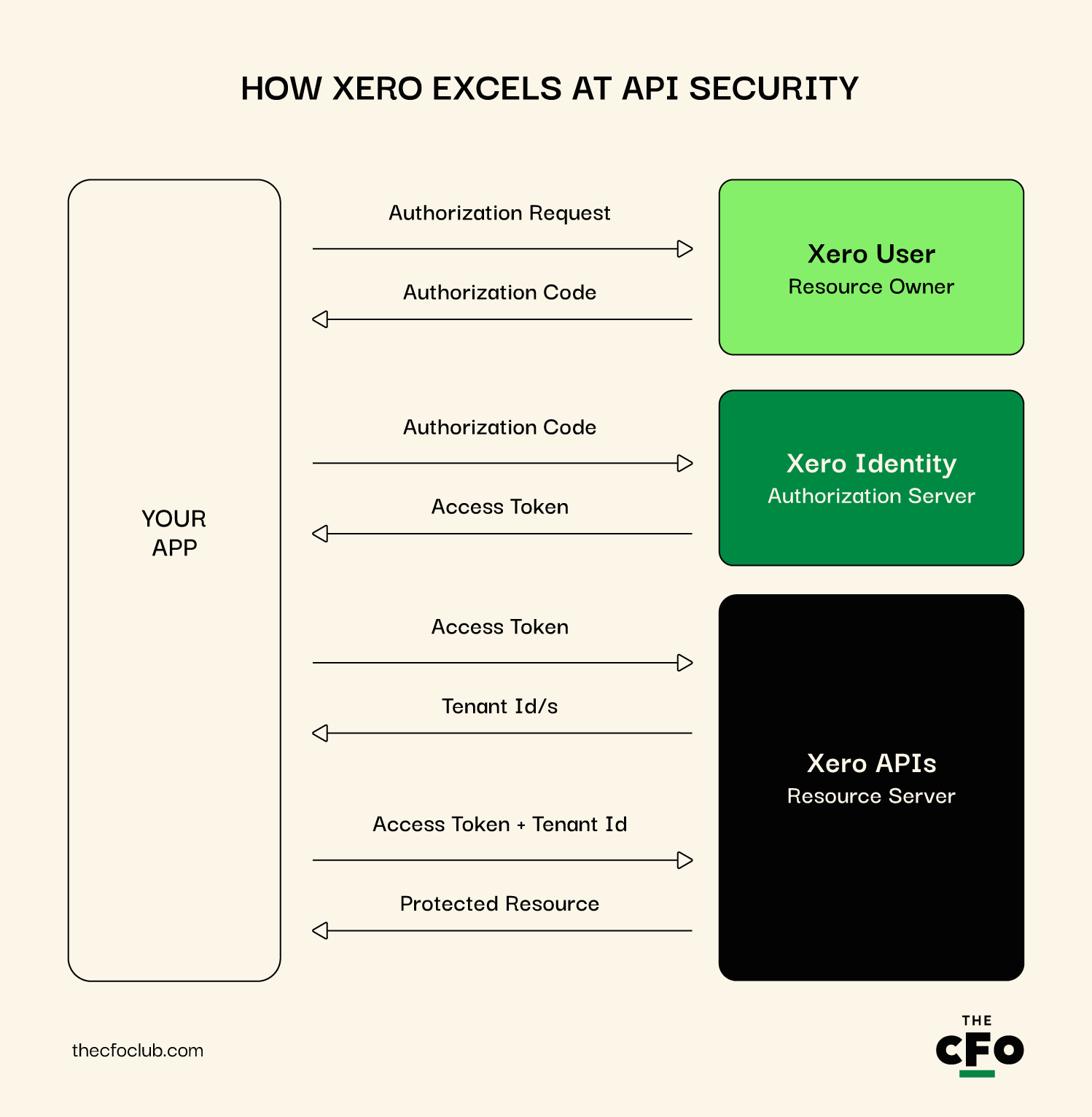
What's impressive about Xero's API strategy is its use of scoped access. This means that when you connect an app to Xero, you can specify exactly what data that app can access. Want an app to read invoices but not touch your bank reconciliation? No problem.
Xero also uses OAuth 2.0 for API authentication, which is considered the industry standard. They provide detailed documentation for developers on how to implement this securely.
14. Educate Employees on Cybersecurity Best Practices
Alright, let's talk about your secret weapon in the fight against cyber threats: your team. All the fancy tech in the world won't save you if someone falls for a phishing scam or uses "password123" for their login.
Here's why employee training is crucial:
- Human error is involved in most data breaches
- Cyber threats are constantly evolving
- Employees are your first line of defense
- A security-aware culture strengthens your overall defense
If you don’t want to sign up for NINJIO, here’s what you can do instead:
- Regular training sessions (at least quarterly)
- Simulated phishing attacks to test awareness
- Clear, easy-to-follow security policies
- Rewards for spotting and reporting potential threats
- Make security part of onboarding for new hires
Treating cybersecurity training as a one-and-done deal is a mistake. It needs to be ongoing and evolving, just like the threats you're facing.
Remember, the goal isn't to make your team paranoid, but to make them cautious and informed. Encourage questions and create an environment where people feel comfortable reporting potential issues.
How Wave Empowers Users
Wave, the free accounting software, takes an interesting approach to user education. They've created a comprehensive "Security Center" within their platform. This isn't just a static page of tips; it's an interactive resource that guides users through security best practices.
Wave has also gamified security to some extent. They have a "security score" feature that rates how well users have secured their account, with suggestions for improvement. It turns security into a positive, proactive task rather than a chore.
15. Adopt Zero Trust Architecture
Adopting a Zero Trust Architecture is like verifying the identity of every person who enters your home, regardless of how often they've visited before. It operates on a "never trust, always verify" principle, ensuring that every request to access your network or data is authenticated and authorized, even if it comes from within the organization.
Threat: Traditional security models often assume trust for internal users, which can lead to breaches if an insider becomes compromised or acts maliciously.
Impact:
- Greater exposure to internal threats and data breaches.
- Increased risk of external attacks exploiting internal trust relationships.
- Difficulty in containing breaches once they occur due to widespread access.
Prevention:
- Verify all access requests: Implement security measures that authenticate and authorize every access request, regardless of the source.
- Use multifactor authentication (MFA): Ensure that MFA is required for all users accessing sensitive systems and data.
- Implement least privilege access: Grant users the minimum level of access necessary for their roles.
- Continuous monitoring and logging: Keep detailed logs of all network activity and regularly review them to detect potential security threats.
Google’s BeyondCorp Model
Google has implemented a Zero Trust security model known as BeyondCorp, which allows employees to work more securely from virtually any location without the need for a traditional VPN.
This model relies on device and user credentials rather than a network perimeter to grant access, significantly enhancing Google’s ability to protect its data and systems from both external and internal threats.
Other Threats To Watch Out For
Here are some additional threats worth keeping an eye on.
- Transaction and audit integrity: Altering financial transactions, tax calculations, or audit logs to embezzle funds, evade taxes, or cover up fraudulent activities.
- Fraud schemes: Insertion of fake invoices and unauthorized payroll modifications, including adding ghost employees, to divert payments or inflate expenses.
- Technology exploits: Exploitation of cloud storage vulnerabilities, API abuse, and IoT device security gaps to access or manipulate sensitive data.
- Advanced manipulation techniques: Use of deepfakes for sophisticated phishing, credential harvesting, and social engineering to steal login information or sensitive data.
- Internal security risks: Insider threats from employees with access to sensitive information, potentially leading to data leaks or sabotage.
What If I Can’t Action These Tips?
Feeling overwhelmed? Don't worry, you're not alone. Implementing robust security measures can be challenging, especially for small businesses or those without dedicated IT staff. Here's what you can do:
- Talk to your vendor: Schedule a security call, ask about built-in features and additional measures.
- Establish a point of contact: Request a dedicated security liaison who understands your needs for quick emergency communication.
- Create a plan: Develop a tailored security roadmap with priorities and timelines. Clarify responsibilities: what your vendor handles vs. what you manage.
- Consider managed services: Explore vendor-offered or third-party security services. Assess the cost versus the risk of a potential security breach.
- Stay informed: Sign up for security updates, attend webinars, and join user forums to learn from peers with similar challenges.
Start with what you can manage and improve gradually. Your vendor should be your partner in this journey.
The Bottom Line: Your Financial Data's Security Is Non-Negotiable
As tech advances, cyber threats are also becoming more sophisticated. Securing your accounting software is non-negotiable for your business' health and integrity.
Security is an ongoing process, not a one-time fix. Whether you're a small business owner doing your own books or a CFO overseeing a large finance department, the principles remain the same: vigilance, education, and implementation are your shields against cyber threats.
Remember, the cost of implementing these security measures is a fraction of what a data breach could cost you - not just in dollars, but in reputation and trust.
Ready to fortify your accounting defenses and stay ahead of cyber threats? Subscribe to our free newsletter for expert security advice, in-depth guides, and insights from finance and cybersecurity leaders shaping the accounting software industry.