Are evil hoodlums trying to drain your bank account? Perhaps your employees are dipping into the till (or the digital equivalent) to issue their own impromptu bonuses? How’s a CFO supposed to keep costs down with this many leaks in the bucket?
Along with ransomware, the biggest cybersecurity risk to businesses under $500 million is fraudsters, with a lot of that danger targeting Accounts Payable (AP) through payment fraud.
But I have good news. These days, the fraud prevention techniques that work best against external crime rings and slippery insiders are mostly the same. I’ll outline the best ways to do this, starting with some necessary context before moving into the strategies and tactics that’ll keep your business funds safe.
An Abridged History of Financial Controls
From the beginning of trade, people have cheated each other. The spread of double-entry bookkeeping, forensic accounting, and trade regulations all help tell the same human story: there will always be people who steal whatever isn’t bolted down.
Over the last century, ledgers have exploded in complexity, enabled by technology, globalization, and a more complicated legal landscape. As the complexity grew, so did the methods for unscrupulous employees to steal money. Accounting circles and associated regulatory bodies responded by developing internal controls, ramping up in the 60s to now become a critical aspect of a well-run business.
In the last 15 years, external threats have dramatically grown. Increasing criminal sophistication, the growing importance of business technology, and a transition toward fast electronic payments have all contributed to the growing global success of scams, ransoms, and theft against businesses.
The Call Came from Inside the House
The most effective way to prevent these new external threats is to increase the governance of your employees because believe me, your biggest threat comes from “inside the house”.
“Are you telling me my staff are untrustworthy?”
No - not always and not on purpose.
Before, the risk of payment fraud came mostly from a combination of employee opportunity, need, and access. An employee with access to company funds is tempted to take advantage, especially if it solves a big problem for them. They then defraud the company and, if they don’t get caught, it often becomes a habit they don’t escape from.
The growth of external fraud adds another factor: the susceptibility of your well-meaning staff to be tricked. “Hacking” is not some techno-wizardry that can magically spirit money out of a bank account; It just gives an already malicious fraudster access by tricking people or systems.
While you can train employees to be more sensitive to attack, extending financial control over their work and systems is one of the best ways to address fraud from either source.
General Strategies
As fraud trends evolve, traditional and internal controls have coalesced into three major strategies to combat payment fraud.
As with any investment, always start with sound risk management: What threats are most likely and most damaging to your business?
1. Reduce Single Points of Failure
This is the engineering version of our old friend, Segregation of Duties (SoD), extending the idea beyond people to target systems and tools. Consider the classic SoD case: If a single employee can disburse funds and edit general ledger entries, that’s dangerous; they represent a Single Point of Failure for payment fraud. After all, it would only take a single thing to fail (them and their ethics) to result in successful fraud.
With modern threats, anything that impersonates them is also a Single Point of Failure: their password, laptop, or even a takeover of their email.
Fix Single Points of Failure by sharing them between a team and adding steps.
This discipline goes deep. In the tactics later in this article, I’ll go over some of the most common Points of Failure and how to address them.
2. Reduce Exposure
There are two major components for reducing your exposure to payment fraud: target sources and target potential impact.
Addressing the source of threats works by reducing the likelihood of the threat occurring; Impact minimizes the potential loss if it does occur.
Consider two classic examples from fraud control: approval limits reduce the potential loss from fraudulent expenses (impact), and least privilege reduces the likelihood of fraud by limiting the number of people that could initiate it (sources).
The cyber industry has a related idea called attack surface, which is usually used to describe systems. It’s a combination of how vulnerable a system is and how many things can connect to it and thus attack it. Cyber teams usually have the most insight into how systems are typically attacked; their challenge usually comes in connecting this idea to actual financial losses. Progress there has accelerated in the last decade.
In my experience, implementing this strategy is often the lowest-hanging opportunity for most organizations to improve their security. Most scams have at least five steps, and fraudsters need to succeed at all to win; To foil them, you only need to stop them at any one of the steps. For each step in a potential fraud scenario, brainstorm how to reduce the sources and impact. Usually, there are several opportunities across all process steps that are free (or nearly so).
Success in this strategy requires rigor (in discovering and documenting processes) and creativity (in brainstorming solutions). The exercise lends itself as a facilitated team-building exercise and often yields efficiency wins as well.
3. Create Actionable Alerts
Building warnings and indicators into processes and systems can stop fraud before it’s too late. In a sense, this is the oldest trick in the book: double-entry bookkeeping, three-way match, and most GAAP leverage independent record-keeping mechanisms to expose problems.
This approach has yielded monumental transformations in many other industries over the last century - from Toyota’s manufacturing revolution to modern product management - with tech companies at the forefront, advocating this approach over the last 15 years. From my experience and the corroboration of finance thought leaders, it has just begun to hit the mainstream. In the last 5 years, many smaller businesses have embraced managing by metrics, and usually assign the CFO to lead that transformation. Lucky you.
But tread thoughtfully: there is a dark side to metrics, dashboards, and alerts. In today’s business world, data abounds. KPIs, SLAs, and status come pre-built on pretty dashboards out of the box. But if the metric or alert does not drive direct action (or worse, drives the incorrect action), it’s worse than useless.
This happens in two ways. First, if there are too many false alerts, teams will become desensitized and ignore them.
Second, some choose metrics that don’t drive direct action. These are often called vanity metrics, and at worst, can give a false sense of security, distracting from real issues. As the lawyers say...
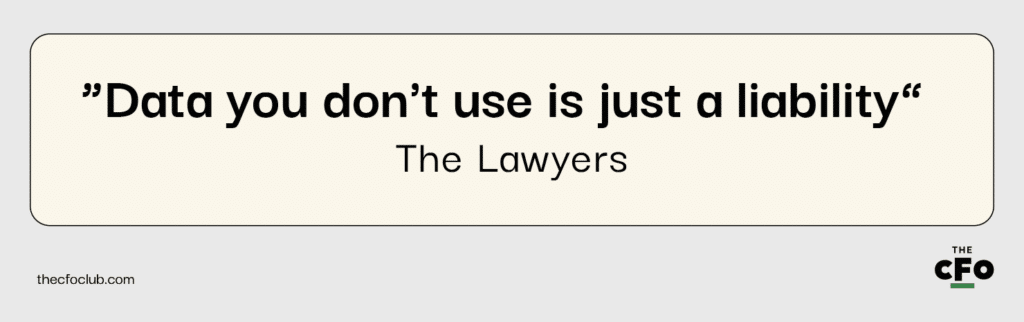
When building alerts, choose events likely to indicate a real problem. A rule of thumb is to only track metrics and alert about them if all stakeholders agree the risk is worth the time to look into it.
Tactics for Preventing Payment Fraud
While there is still tremendous value in the tried-and-true conventional internal controls, some can be prohibitive for all but the largest organizations. I’ve found the following mechanisms to be especially effective at stopping modern fraud in smaller organizations, often for surprisingly little effort. These controls are roughly prioritized, but value and effort will vary widely between companies.
1. Segment Accounts
Strategy: Reduce Exposure
This is a mainstay but still underused for growing businesses. Isolating bank accounts for payments can prevent extreme losses. Keep a dedicated account for one-off payments, another account for predictable monthly expenses, and a treasury account for other funds.
Maintain a low balance in the predictable account, manually provision funds to the one-off account, and never pay out of the treasury account. Any fraud that hits either payables accounts will incur either nominal losses or fail completely.
This control can be made easy with AP automation platforms.
2. Business Credit Agency Registration
Strategy: Reduce Exposure
This one is easy and addresses a different type of fraud: identity theft of your business. False credit can be taken out in your business’s name and cleanup can be a chore. Registering with business credit agencies first can make it much harder for criminals to take advantage of you in this way.
3. Move Off Email
Strategy: Reduce Single Points of Failure
Email enables a huge amount of fraud and crime. It’s little wonder, as many organizations run almost everything over it. If this describes your business, email is a likely single point of failure for you: if a fraudster gets into your email, they could cause a lot of damage while covering their tracks.
Fixing this is easy: only use dedicated systems to perform high-risk activities.
4. Single-Sign-On, Multi-Factor Authentication
Strategy: Reduce Single Points of Failure
This one is a little techy, but well worth it. The best way of doing passwords, federation, eliminates a huge number of Single Points of Failure for criminal impersonation on your systems. What you want is a modern, central system that acts as an identity provider for your staff; you’ll then tell each system you use to trust it. Workers log in to the identity provider, and then everything else magically connects.
As I mentioned, it is technical, so your IT team will need to build the connections.
Passwords are a common point of failure, so requiring strong multi-factor authentication (MFA) eliminates that. Any federation provider worth their salt will also strongly advise you to require it.
5. Honeypots
Strategy: Actionable Alerts
Honeypots (sometimes called canary tokens) are an approach that tells you if a cybercriminal got past all your protection and into something they shouldn’t. Honeypots are decoys that send automatic alerts when used. It is most widespread in tech but can be created for payment details as well. This can work especially well with automated finance platforms, which I mention in tactic #10.
Tech honeypots are easy and free to set up.
6. Outsource to a Service
Strategy: Reduce Single Points of Failure
Using a vendor is often not only cheaper than you can deliver in-house but also more resilient. Outsourcing can remove many single points of failure by spreading your company’s needs across a larger team and system.
Many companies find that an Accounts Payables service becomes the cheaper option when AP takes up half the time of an employee. Because this estimation ignores the cost of fraud, I often recommend companies consider this well before that point. Some automation platforms can allow a finance team to scale their volume 100x without new headcount or loss of control.
Outsourcing your IT systems to a web platform can be another excellent way to remove single points of failure. They will do a reliably better job with encryption, malware and vulnerabilities identification, data breach resistance, and phishing prevention than you likely have the capacity to do in-house.
This only works if the outsourcing offering has few or no single points of failure. Many finance outsourcers provide a dedicated, fractional do-everything accountant who works in your systems and does your processes - not a good option if you’re looking to decrease risk. Likewise, a good number of web platforms continue to build with the same fragile designs used in 2006, add cloud buzzwords to their marketing, and hope nobody looks under the hood. Needless to say, neither of these provides security benefits.
7. Virtual Cards
Strategy: Reduce Exposure
Using a virtual card provider allows granular control over who you pay, and how much you can pay them. I covered virtual cards already in my article explaining how to secure B2B payments. Most Automated AP platforms provide virtual cards.
8. Vendor Validation and 3-way Match
Strategy: Reduce Exposure
Restricting payments to a list of authorized vendors, validating payment information, and matching invoices to purchase orders can help eliminate a lot of the less sophisticated fraud. Many providers provide matches to a list of vetted vendors; this can be surprisingly cheap.
9. Positive Pay
Strategy: Reduce Exposure
This feature allows you to send a list of authorized purchase orders to your bank each month. The bank then blocks ACH and check payments that do not match, and notify the business when it does. This mechanism got a reputation 20 years ago as a lot of work, but many offerings have since smoothed most kinks out.
10. Automated Finance
Strategy: Actionable Alerts & Reduce Single Points of Failure
An automated finance platform can allow you deeply granular control over how money moves at your organization with a fraction of the staff. It can be tremendously valuable but often is an expensive transition. Consider:
- Automatic payments to consistent, long-term vendors. You can usually configure the payment details within the vendor record.
- Automatic invoicing and dunning
- Automated transfers and receivables
- Alerts for unexpected transactions and balances
- Automatic invoice and 3-way or 2-way match processing
- AI/Anomaly detection (information below)
Some platforms magically alert you about risky transactions, based on current industry threats and what general ledger activity is normal for your business. My advice? If you want a product because of its anomaly detection feature, take it for a spin first. AI products are always black-box, so you can’t objectively measure quality. Black-box product effectiveness also tends to degrade over the years, as threats and conditions evolve.
Tech Products for Accounts Payable
This is a selection of new and established AP platforms with features that I’ve mentioned in this article. Banks also provide Outsourced AP and Outsourced AR (often billed as Remittance Processing), usually white-labeled from a dedicated provider.

Fraud is Avoidable
You can eliminate a lot of damage from internet crime by implementing strong internal controls over AP. While external threats have exploded in the last decade, the tools to detect and prevent them have also grown.
For more tips for financial operators, including how to keep your business safe from online threats, subscribe to The CFO Club newsletter today.
I would love to hear from you: what controls have been most effective in preventing fraud? Have you done any of these? Let me know in the comments or on social media.