It’s the climax of a fictional big-budget war movie and the President has just approved the emergency launch of a nuclear warhead. The somber officers begin the launch sequence by retrieving two keys, turning them dramatically slowly.
As cliché as this scene is, it reflects a real process within the U.S. military. The so-called Two Man Rule, established during the Cold War, ensures that access to sensitive weaponry will always require the input of two separate high-ranking individuals, even once it’s been verbally approved by the commanding officer.
And it’s not just the military. Two-person control protocols are employed by governments, banks, security firms, asset managers, and pharmaceutical companies, to name just a few.
The idea is to reduce the risk of error, fraud, or malicious behavior by dividing responsibility for key actions between two or more parties. The basic concept is known as segregation of duties — and it’s crucially important to tech firms. Here’s why.
What Is Segregation Of Duties?
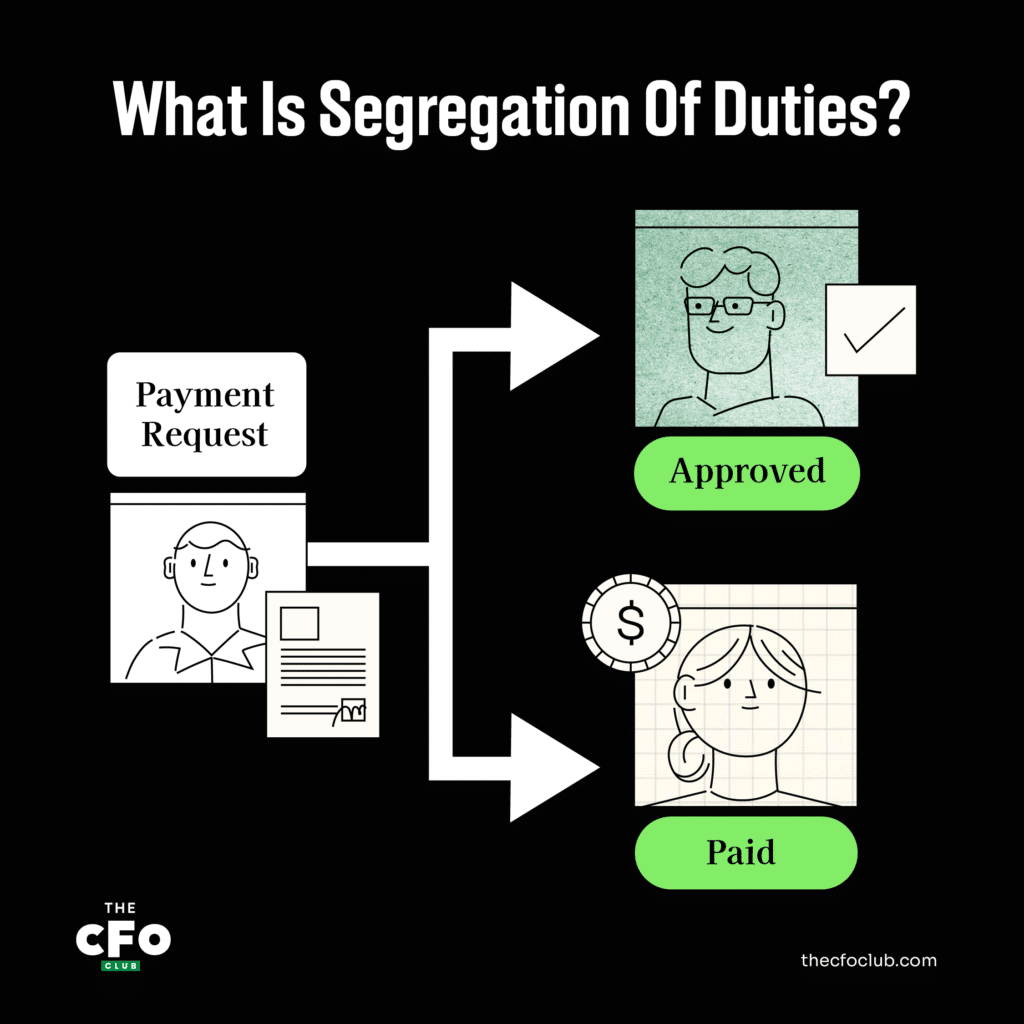
Segregation of duties (SoD) is an internal control that ensures that at least 2 individuals are jointly responsible for a given task. It’s usually implemented by assigning 2 or more individuals to handle separate components of a specific task.
For instance, a CFO might decide to delegate payroll accounting to Employee A, but have Employee B sign off on the actual paycheck processing.
The idea is to help reduce the risk of fraud and human error by ensuring no single entity has full control over any important process. Segregation of duties is also referred to as separation of duties — the terms may be used interchangeably.
Generally speaking, there are 4 main roles or types of activities that should ideally be segregated. This means that no single entity should be responsible for all 4 of these activities; and in an ideal scenario, each should be handled independently. These categories are:
Authorization or Approval (AUT)
The individual who authorizes a transaction, order, or significant internal action, and/or the person who approves said action.
Custody of Assets (CUS)
The individual responsible for maintaining assets, such as inventory or a physical check from a client.
Recording Transactions (REC)
The individual who records transactions in an accounting system or other internal record.
Reconciliation/Control/Verification (VER)
The individual who reconciles bank account records, physical inventory levels, etc.
SoD protocols are relevant enterprise-wide, but the most significant applications are in risk management and accounting. These protocols apply equally in a corporate setting, nonprofit, or government agency.
Some examples of segregation of duties are found below.
Risk Management
Risk management teams may segregate duties by:
- Having multiple stakeholders sign off on any major IT changes, website updates, etc.
- Ensuring internal review processes (involving multiple stakeholders) are implemented prior to the publication of any financial statements (to ensure compliance with SOX regulations)
- Ensuring sensitive internal comms and trade secrets are monitored and restricted to employees with appropriate clearance
- Having those responsible for IT security share responsibility for setting role-based access controls
Accounting
Some examples of accounting teams segregating duties are:
- Having separate employees handle payroll accounting and payroll processing
- Tasking one employee with maintaining inventory records, and another with physically possessing and processing said inventory
- Having one employee sign off on the receipt of physical goods, and another process the payment for said goods
Other Functions
Segregation of duties may also apply during the hiring process (to prevent nepotism), during the firing or layoff process (to prevent sabotage or other malicious behavior), and in various other human resources settings.
Why It's Worth The Hassle
The main drawback of SoD — and the reason some firms skip out on it — is that it has a tendency to bottleneck certain processes. By definition, SoD separates tasks that one person could theoretically perform, which can create what could be viewed as inefficiencies.
But skimping out on SoD protocols can have devastating consequences.
For one, it opens up the door to payment fraud, embezzlement, and theft. If a single person is tasked with placing orders, receiving orders, approving payments, and reconciling records, the opportunity for nefarious activity is far too accessible.
The prospect of internal fraud may seem far off, but it’s a very real threat to most businesses. A 2022 report by the Association of Certified Fraud Examiners found that worldwide, organizations lose 5% of revenue to fraud annually — and fraud committed by employees was both the most common and the most costly.
Two, it increases the odds of human error impacting your business. If you don’t have a second set of eyes on important internal processes, your chances of missing mistakes go up dramatically.
And third, it makes for less effective internal controls. By allowing unilateral decisions and actions, the chances of any one person creating havoc in your business (intentionally or unintentionally) increases.
Best SoD Practices
Best practices for the segregation of duties will look different depending on the size of the firm. Smaller firms may have to sacrifice some SoD protocols simply due to the smaller team sizes.
That said, there are some general guidelines for best practices, including:
Implementing SoD on multiple levels: Depending on the size of the firm, organizations may wish to implement SoD not only on an individual level but also on a departmental and company/subsidiary level. For instance, investments made by a subsidiary may require approval from a parent company, or a sales department may require a sign-off by the operations department before final approval.
Using a SoD matrix: A segregation of duties matrix is a simple table graph that plots user groups and respective procedures/roles on both the X and Y axes. Appropriate roles are marked with a checkmark, which helps to easily identify incompatible duties. Below is an example of a SoD matrix for a payroll function.
| Procedure | User group | Create paycheck | Change compensation | Change benefits | Approve paycheck |
|---|---|---|---|---|---|
| Create paycheck | A | ✓ | |||
| Change compensation | B | ✓ | ✓ | ||
| Change benefits | C | ✓ | ✓ | ||
| Approve paycheck | D | ✓ |
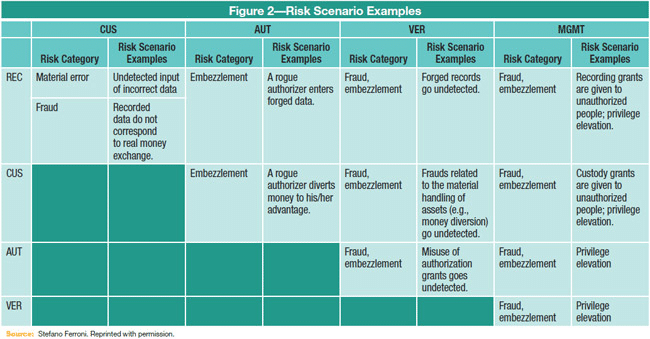
Identifying risk scenarios: Some risk scenarios are obvious, while others require more careful research. The table below lays out common risk scenarios and the overlap in roles (reminder: CUS = custody, AUT = authorization, VER = verification, REC = recording)
Conducting ongoing SoD audits: Segregation of duties is not a one-and-done process, but rather an ongoing operational guideline for your entire operation. Conducting regular audits of internal controls, including SoD frameworks, is important for long-term success.
Recording — and penalizing — SoD violations: A SoD violation occurs when an individual abuses their role and access level to bypass SoD protocol (typically, this is a deliberate action). This could be a violation of an internal company policy, or an external regulatory requirement. In any case, it’s vital that SoD violations are identified and recorded, and that the responsible individual be reprimanded if necessary.
Setting minimum thresholds to avoid red tape: This isn’t necessarily a best practice, but rather a workaround that some smaller firms choose to implement. To keep everyday operations running smoothly, some firms choose to set minimum thresholds (usually in dollar terms) for transactions that can be processed outside of standard SoD controls. For instance, a manager may authorize team members to approve and pay for qualifying expenses under $500, without external approval. These kinds of small-fry exceptions allow teams to stay more focused on the bigger picture.
Utilize internal and external auditing: Routine auditing is important for any business. While many tasks can be handled in-house with the help of audit management software, bringing in external auditors and consultants can be worthwhile as well. A skilled consultant can take a detailed and entirely impartial look at the inner workings of your organizational structure, workflows, and employee access levels to identify vulnerabilities that your team may have missed (or worse, hidden).
Tools That Help Segregate Duties
Segregation of duties procedures can be assisted by various tools, including software and external consultants/auditors.
Software Tools for SoD
In some cases, enterprise software will have SoD frameworks built in to help teams create a SoD matrix, identify potential conflicts, and even monitor and record violations.
Enterprise resource planning (ERP) software from the likes of Oracle, Sage, and SAP often have segregation of duties features built in. Enterprise risk management software may also benefit teams. Feature sets vary depending on the software provider and even the tier of service subscribed to, but generally speaking, these tools can benefit teams working towards SoD best practices.
There are also software solutions built specifically for SoD compliance, internal access controls, and internal SoD policy management.
Segregation of Duties Auditing/Consultants
As I mentioned, bringing in auditors may also be wise. This can be done independently or as part of a larger internal audit.
Many auditing firms offer SoD auditing services. Specialist consultants may also offer support for the initial implementation of a SoD framework.
SoD: A Proven Method Of Organizational Checks And Balances
Like the multiple branches of the government, segregation of duties is intended to create a system of checks and balances. If implemented correctly, SoD frameworks can reduce the risk of fraud, malicious acts, corporate espionage, and simple human error.
Looking for more valuable insights into corporate finance for tech firms? The CFO Club Newsletter provides valuable information weekly from finance leaders, for finance leaders — for free. Subscribe today.